Analysis of OpenID implementations
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report to Moderator
- Plusnet Community
- :
- Plusnet Blogs
- :
- Analysis of OpenID implementations
Analysis of OpenID implementations
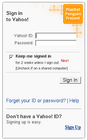
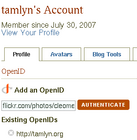
Update: Added review of VeriSign's offering below. As Kelly mentioned yesterday, I have spent a few hours looking at how other sites have implemented their OpenID interfaces. Yahoo!'s new service was my favourite because it explains everything and makes it very clear and simple. On the other hand it lacks some features that I think are essential. Identity providers Yahoo!
- slickest design
- least features (cannot 'remember' authenticated sites)
- lots of useful explanatory text
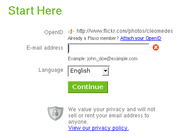
- login to the service with the standard Yahoo! login screen which benefits from anti-phishing protection
- the default OpenID URI they give you is hideous (e.g. https://me.yahoo.com/a/cNS2XuhgzObzs5svX5owhplR09A_feaT) but you have the option to choose an alternative one such as a Flickr profile (e.g. http://flickr.com/photos/username)
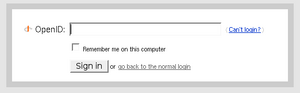
- supports only OpenID 2.0, not 1.1 - this means you can't use it for any sites that have not yet been upgraded to OpenID 2 (most of them at present)
- OpenID support is hidden away & difficult to access
- has the option to 'Remember this site' but doesn't seem to provide any mechanism to manage authenticated sites
- supports OpenID 1.1
- most feature-rich implementation
- supports both OpenID 1.1 and 2.0
- fairly simple to use but extra features inevitably add complexity to the interface
- more than just OpenID, something like a digital life aggregator or lifestream
- supports only OpenID 1.1
- allows users to edit the details that will be sent for Simple Registration requests
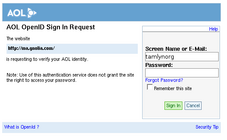
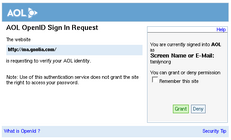
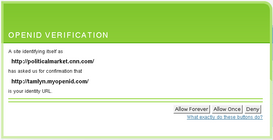
Updated: VeriSign Personal Identity Provider
- OpenID 1.1
- more features & options that most users are likely to need (or understand)
- some advanced features tying-in with VeriSign's security features
- very granular control of the personal information exposed to the relying party via Simple Registration
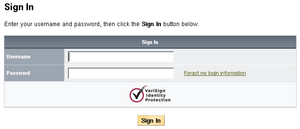
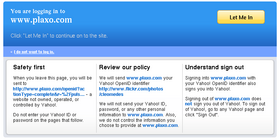
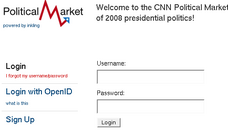
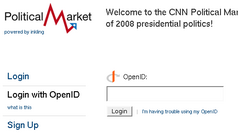
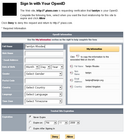 Relying parties (OpenID consumers) Plaxo
Relying parties (OpenID consumers) Plaxo
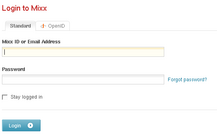
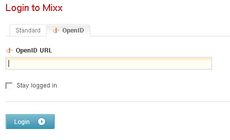
- supports OpenID 1.1 and 2.0
- supports Simple Registration extension which makes signup a breeze
- nice login/signup screens
- doesn't work!
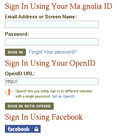
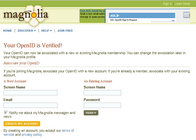
- on first use can create screen name or associate with existing account
- can associate several OpenIDs with one Ma.gnolia account which seems a bit unnecessary
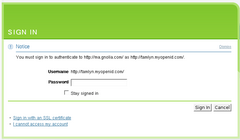
- must sign up for an account before being able to use OpenID
- login screen remembers your choice of OpenID as preferred system
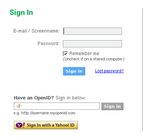
- tabbed login screen
- prize for most amusing error message: "While we're pretty sure that you exist, your OpenID provider says that you don't. Will you try again, please?"
- Didn't work for me
- supports OpenID 2.0
- login fails completely if Simple Registration is not supported
- simplest, no-nonsense system
- supports Simple Registration
- doesn't ask to reconfirm registration details, upon returning to the site you are already registered & ready to go
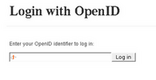
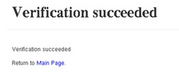 Conclusions Yahoo! has done an excellent job at making OpenID easier to understand for less techy folks. Plaxo has probably the best implementation of an OpenID consumer. VeriSign demonstrates the use of advanced security features as well as improved phishing detection using a browser extension. Directed identity in OpenID 2.0 affords a much improved user experience. Instead of remembering an arbitrary URL such as me.yahoo.com/something, users need only remember the URL of the identity provider, in the case yahoo.com. Everything else happens behind the scenes. Few sites currently support OpenID 2.0 and there is no way of tellin, at sign-in, which version of OpenID the relying party supports. This will undoubtedly create confusion especially since OpenID 2.0 support does not guarantee OpenID 1.1 support. The recommended option is to support both versions.
Conclusions Yahoo! has done an excellent job at making OpenID easier to understand for less techy folks. Plaxo has probably the best implementation of an OpenID consumer. VeriSign demonstrates the use of advanced security features as well as improved phishing detection using a browser extension. Directed identity in OpenID 2.0 affords a much improved user experience. Instead of remembering an arbitrary URL such as me.yahoo.com/something, users need only remember the URL of the identity provider, in the case yahoo.com. Everything else happens behind the scenes. Few sites currently support OpenID 2.0 and there is no way of tellin, at sign-in, which version of OpenID the relying party supports. This will undoubtedly create confusion especially since OpenID 2.0 support does not guarantee OpenID 1.1 support. The recommended option is to support both versions.